Introduction to Post-Quantum Cryptography for Technologists
This comprehensive tutorial covers post-quantum cryptography (PQC), a critical evolution in securing digital systems against the emerging threat of quantum computers. We’ll build from cryptographic fundamentals through practical implementation strategies across multiple domains including financial services, healthcare, telecommunications, and IoT systems. This guide assumes basic familiarity with digital security concepts while explaining advanced topics from first principles.
Disclaimer: This article is provided for educational purposes only and should not be construed as professional security consulting, legal advice, or technical recommendations for specific implementations. The rapidly evolving nature of quantum computing and post-quantum cryptography means information may become outdated. Where appropriate, I will reference real-world implementation approaches, including those pioneered by companies like BTQ Technologies, to illustrate practical applications without specifically endorsing any particular solution. Such references to specific companies or technologies are provided as illustrative examples only and do not constitute endorsements. Readers should consult qualified security professionals and refer to official standards bodies (such as NIST) before making cryptographic implementation decisions. The author assumes no liability for actions taken based on this information.
Important Distinction: Quantum Cryptography vs. Post-Quantum Cryptography
A critical clarification: quantum cryptography and post-quantum cryptography are fundamentally different and often confused.
Quantum Cryptography (QC)
Quantum cryptography uses quantum mechanical properties for cryptographic tasks. The most well-known example is Quantum Key Distribution (QKD).
Key characteristics:
- Requires quantum hardware: Uses photons, quantum states, and specialized communication channels
- Physical infrastructure: Needs quantum repeaters, specialized fiber optics, or satellite links
- Limited range: Currently restricted to hundreds of kilometers without quantum repeaters
- Theoretical advantage: Eavesdropping disturbs quantum state, making interception detectable
- Primary use: Secure key distribution only
Example: Alice sends Bob photons in specific quantum states through fiber optics. If Eve intercepts, the quantum state collapses, introducing detectable errors.
Post-Quantum Cryptography (PQC)
Post-quantum cryptography (this article’s focus) consists of classical cryptographic algorithms designed to resist attacks by both conventional and quantum computers. These mathematical algorithms run on standard computers.
Key characteristics:
- Runs on classical computers: No quantum hardware required—works on existing infrastructure
- Drop-in replacement: Can replace existing algorithms (RSA, ECDSA) in current systems
- Based on hard math problems: Uses lattices, hash functions, or coding theory problems
- Practical deployment: Works over existing internet infrastructure
- Full functionality: Supports encryption, digital signatures, and key exchange
Example: A financial system uses ML-DSA (Dilithium) to sign transactions. The signature is generated and verified using standard processors. Even when quantum computers exist, attackers cannot forge signatures because the underlying lattice problem remains computationally hard.
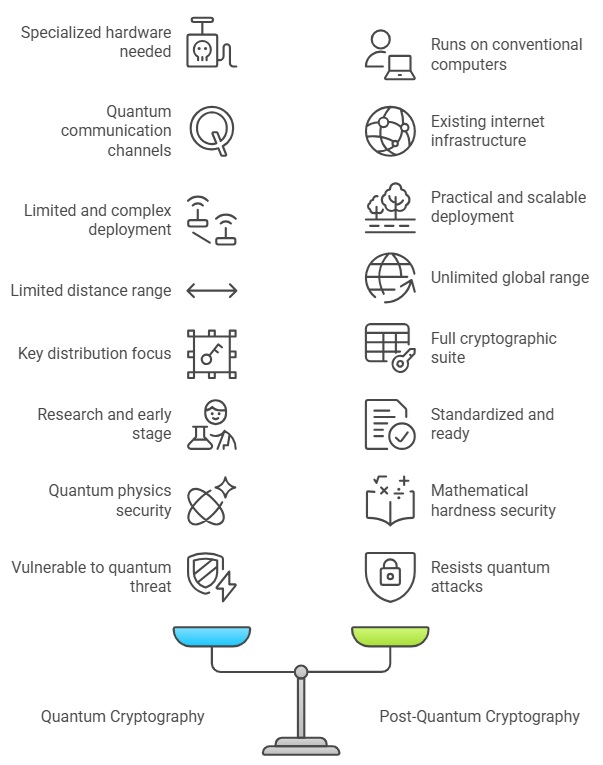
Key Differences
| Aspect | Quantum Cryptography (QC) | Post-Quantum Cryptography (PQC) |
|---|---|---|
| Hardware | Requires specialized quantum hardware | Runs on conventional computers |
| Infrastructure | Needs quantum communication channels | Works with existing internet |
| Deployment | Limited, expensive, complex | Practical, scalable, deployable today |
| Use Cases | Primarily key distribution (QKD) | Full cryptographic suite |
| Maturity | Research/early commercial stage | Standardized by NIST, ready |
| Security Basis | Laws of quantum physics | Computational hardness |
Common misconception: “To defend against quantum computers, we need quantum technology.”
Reality: Post-quantum cryptography provides practical defense using conventional technology available today.
This article focuses exclusively on post-quantum cryptography (PQC)—the practical solution organizations should implement now to protect against quantum computing threats.
Table of Contents
- Understanding Cryptography Fundamentals
- The Quantum Computing Threat
- Introduction to Post-Quantum Cryptography
- PQC Implementation Strategy
- Real-World Implementation Considerations
- Safety and Security Considerations
- Review of Key Concepts
- Conclusion
1. Understanding Cryptography Fundamentals
Cryptography secures information by transforming it into an unreadable format that only authorized parties can reverse. It protects everything from online banking to government secrets.
1.1 What is Cryptography?
At its core, cryptography involves three operations:
- Encryption: Converting readable data (plaintext) into unreadable format (ciphertext)
- Decryption: Converting ciphertext back to plaintext
- Key Management: Securely generating, distributing, and storing cryptographic keys
Think of encryption like putting a letter in a locked box. The plaintext is your letter, the ciphertext is the locked box, and the key unlocks it. Without the key, intercepting the box reveals nothing.
1.2 Public-Key Cryptography
Modern systems rely on public-key cryptography (asymmetric cryptography), using two mathematically related keys:
- Public key: Can be shared openly
- Private key: Must be kept secret
This works through mathematical operations that are easy to perform in one direction but extremely difficult to reverse.
Example: Imagine a special mailbox where anyone can drop letters through the slot (using your public key to encrypt), but only you have the key to open and read them (using your private key to decrypt).
1.3 Common Cryptographic Algorithms
RSA (Rivest-Shamir-Adleman):
- Based on difficulty of factoring large numbers
- Easy to multiply 61 × 53 = 3,233, but hard to determine 3,233 came from 61 and 53
- With hundreds of digits, practically impossible for classical computers
- Used for: Digital signatures, key exchange, encryption
ECDSA (Elliptic Curve Digital Signature Algorithm):
- Based on elliptic curve discrete logarithm problem
- Uses mathematical properties of elliptic curves
- More efficient than RSA—similar security with smaller keys
- Used for: Digital signatures, authentication, blockchain transactions
These algorithms have protected digital infrastructure for decades because even the fastest conventional computers would take thousands of years to break them.
But quantum computers change everything.
“The science of today is the technology of tomorrow.” ~ Edward Teller
2. The Quantum Computing Threat
2.1 What Makes Quantum Computers Different?
Classical computers process information in bits (0 or 1). An 8-bit classical computer represents one of 256 possible values at any moment.
Quantum computers use qubits that exist in superposition—simultaneously being both 0 and 1 until measured. Like a spinning coin being both heads and tails until it lands.
This difference is profound:
- 8 classical bits: 1 value at a time
- 8 qubits: All 256 values simultaneously
As you add qubits, computational power grows exponentially. A 300-qubit quantum computer could theoretically perform more calculations simultaneously than there are atoms in the observable universe.
2.2 Shor’s Algorithm: Breaking Current Cryptography
In 1994, Peter Shor demonstrated that quantum computers could efficiently solve the mathematical problems underlying RSA and ECDSA security.
Shor’s Algorithm can:
- Factor large numbers exponentially faster than classical computers
- Solve the elliptic curve discrete logarithm problem efficiently
- Break RSA and ECDSA that would take classical computers millennia to crack
What this means: A quantum computer with sufficient qubits could break current cryptography in hours that would take classical computers thousands of years.
Current estimates:
- 20 million qubits: Could break RSA-2048 in ~8 hours
- 1 million qubits (with error correction): Could break common elliptic curve cryptography
2.3 Timeline: When Will This Happen?
The quantum computing community refers to “Q-Day”—when a quantum computer becomes powerful enough to break current cryptographic systems.
Current predictions:
- Cybersecurity experts: 1 in 3 predict Q-Day before 2032
- Conservative estimates: 2030-2035
- Some experts: Could be secretly achieved even sooner
Recent milestones:
- Google’s Willow chip (December 2024): Demonstrated quantum error correction improvements
- IBM’s quantum processors: Approaching 1,000+ qubits
- Recent research: Reduced qubit requirements from 20 million to under 1 million for breaking RSA
2.4 The Harvest Now, Decrypt Later Attack
The most immediate threat: adversaries don’t need to wait for Q-Day.
The “Harvest Now, Decrypt Later” (HNDL) strategy:
- Today: Attackers intercept and store encrypted data
- Tomorrow: When quantum computers available, decrypt stored data
- Impact: Information that seems secure today will be exposed
Why this matters:
- Medical records remain sensitive for 50+ years
- Financial records have long-term value
- Government secrets may be classified for decades
- Personal communications could be used for future blackmail
The U.S. Federal Reserve (September 2025) explicitly warned that HNDL attacks are “present and ongoing”—not hypothetical.
2.5 Vulnerable Systems
Nearly all current digital security is at risk:
- Financial systems: Banking transactions, payment cards, digital assets
- Communications: Encrypted messages, VPNs, secure channels
- Authentication: Digital signatures, certificates, identity verification
- Blockchain: Bitcoin, Ethereum, smart contracts
- Government systems: Classified communications, defense systems
- Healthcare: Electronic health records, medical devices
- Critical infrastructure: Power grids, water systems, transportation
The scope is staggering: virtually every secure digital system today relies on cryptography that quantum computers will break.
“We cannot solve our problems with the same thinking we used when we created them.” ~ Albert Einstein
3. Introduction to Post-Quantum Cryptography
3.1 What is Post-Quantum Cryptography?
Post-quantum cryptography (PQC) refers to cryptographic algorithms believed secure against attacks by both classical and quantum computers. Unlike current algorithms relying on factoring or elliptic curves, PQC uses different mathematical foundations that quantum computers cannot easily break.
Key characteristics:
- Based on problems that remain hard even for quantum computers
- Runs on classical (conventional) computers—no quantum hardware needed
- Designed to replace current algorithms in existing systems
- Standardized by organizations like NIST
3.2 Mathematical Foundations of PQC
PQC algorithms resist quantum attacks through hard mathematical problems:
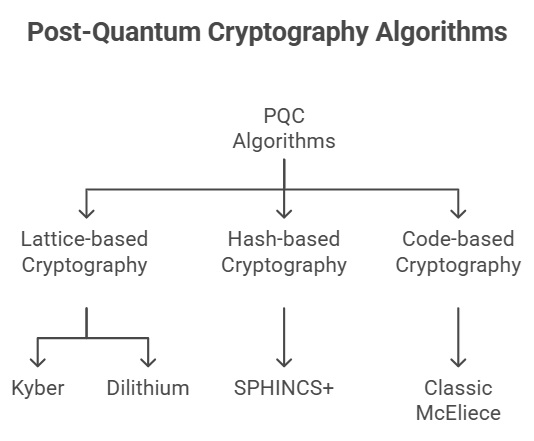
1. Lattice-based cryptography:
- Based on finding shortest or closest vector in high-dimensional lattice
- Like finding shortest path through complex 3D jungle gym, but in hundreds of dimensions
- Examples: Kyber (key exchange), Dilithium (digital signatures)
- Why quantum-resistant: Quantum computers struggle with high-dimensional geometric problems
2. Hash-based cryptography:
- Uses cryptographic hash functions (one-way transformations)
- Like grinding coffee beans—easy to grind, impossible to reconstruct beans from powder
- Example: SPHINCS+ (digital signatures)
- Why quantum-resistant: Hash functions remain secure against quantum attacks
3. Code-based cryptography:
- Based on difficulty of decoding general linear codes
- Like solving complex puzzle with astronomical arrangement possibilities
- Example: Classic McEliece (key exchange)
- Why quantum-resistant: Underlying problems not vulnerable to known quantum algorithms
3.3 NIST Standardization
In August 2024, NIST published the first three post-quantum cryptographic standards:
FIPS 203 (ML-KEM, formerly Kyber):
- Type: Key Encapsulation Mechanism
- Use: Securely establishing shared secret keys over public networks
- Based on: Module Learning with Errors (lattice problem)
FIPS 204 (ML-DSA, formerly Dilithium):
- Type: Digital Signature Algorithm
- Use: Verifying authenticity and integrity of digital documents
- Based on: Module lattices
FIPS 205 (SLH-DSA, formerly SPHINCS+):
- Type: Stateless Hash-Based Digital Signature
- Use: Alternative signature algorithm not based on lattices
- Based on: Hash functions
Additionally, FN-DSA (Falcon) is progressing toward standardization as a fourth digital signature algorithm.
3.4 Why Migration is Urgent
Federal mandates create hard deadlines:
-
NSM-10 (May 2022): All U.S. federal systems must mitigate quantum risk by 2035
-
CNSA 2.0 (September 2022):
- New systems must support PQC from January 1, 2027 (just over 1 year away!)
- Complete phase-out of non-PQC by December 31, 2030
- All systems quantum-resistant by 2035
-
RSA/ECDSA deprecation:
- Deprecated after 2030
- Disallowed after 2035
The exposure window:
Consider hardware deployed today with 10-year lifespan:
- Deployment: 2025
- Lifespan: Until 2035
- HNDL storage: 5 years
- Q-Day: 2030-2035
- Total exposure: Data collected 2025 remains vulnerable until 2040
Any long-lifespan hardware deployed between now and 2030 needs quantum-safe protection from day one.
“An investment in knowledge pays the best interest.” ~ Benjamin Franklin
4. PQC Implementation Strategy
Successfully transitioning to PQC requires careful planning and execution.
4.1 Assess Current Systems
Create a cryptographic inventory:
-
Identify cryptographic usage:
- Encryption (data at rest, in transit, backups)
- Authentication methods (passwords, certificates, tokens)
- Digital signatures (document signing, code signing, transactions)
- Key exchange mechanisms (TLS/SSL, VPNs, secure messaging)
-
Document existing algorithms:
- RSA key sizes and usage
- ECDSA curves and applications
- Hash functions (SHA-256, SHA-3)
- Symmetric encryption (AES is quantum-safe and can remain)
-
Assess system constraints:
- Computational resources available
- Bandwidth limitations
- Storage capacity
- Real-time performance requirements
-
Prioritize based on risk:
- Data with long-term sensitivity (medical, financial)
- High-value targets (payment systems, credentials)
- Systems with long lifecycles (IoT devices, infrastructure)
- Internet-facing services (most vulnerable to interception)
4.2 Select Appropriate Algorithms
Key considerations:
-
Security level:
- NIST defines five levels (1-5)
- Level 1 ≈ AES-128 (sufficient for most applications)
- Level 3 ≈ AES-192 (moderate security)
- Level 5 ≈ AES-256 (high security for sensitive data)
-
Performance characteristics:
Algorithm Public Key Signature Performance RSA-2048 (current) 2,048 bits 2,048 bits Baseline ML-DSA-65 (Dilithium) ~1,952 bytes ~3,293 bytes Fast FN-DSA (Falcon-512) ~897 bytes ~690 bytes Very fast SLH-DSA-128f ~32 bytes ~17,088 bytes Slower -
Algorithm selection guidelines:
For key exchange:
- ML-KEM (Kyber): First choice for most applications
- Security levels: 128, 192, 256 bits
- Excellent performance with reasonable key sizes
For digital signatures:
- ML-DSA (Dilithium): General-purpose, good performance
- FN-DSA (Falcon): When signature size matters (blockchain, IoT, satellite)
- SLH-DSA (SPHINCS+): Long-term security and algorithmic diversity
4.3 Plan Migration Strategy
Migration approaches:
1. Hybrid approach (recommended):
- Use both classical and post-quantum algorithms simultaneously
- Requires both signatures to validate
- Provides security if either algorithm is compromised
- Doubles signature size but ensures safety during transition
2. Phased rollout:
Phase 1: Infrastructure preparation (Months 1-3)
- Update cryptographic libraries
- Test PQC algorithms in development environments
- Train teams
- Establish performance baselines
Phase 2: Low-risk deployment (Months 4-6)
- Deploy to internal systems first
- Enable PQC for new keys and certificates
- Monitor performance and compatibility
Phase 3: Critical system migration (Months 7-12)
- Migrate high-value systems
- Implement hybrid approach for maximum security
- Intensive monitoring
Phase 4: Complete transition (Months 13-24)
- Deprecate classical-only cryptography
- Full PQC deployment
- Continuous security auditing
3. Backward compatibility:
- Maintain support for classical cryptography during transition
- Use protocol negotiation (systems agree on strongest mutually supported algorithm)
- Plan for extended transition period (2-5 years for large organizations)
4.4 Optimize Performance
PQC algorithms have different performance characteristics than classical cryptography.
Performance considerations:
-
Computational overhead:
- PQC operations typically slower than RSA/ECDSA
- Lattice-based algorithms require polynomial mathematics
- Hash-based algorithms require many hash computations
-
Size trade-offs:
- PQC keys often 5-10x larger than classical equivalents
- Impacts storage, bandwidth, and transmission time
- Particularly important for: blockchain (storage cost), satellite (bandwidth constraints), IoT (memory limits)
Optimization strategies:
Hardware acceleration:
- Standard CPUs optimized for general computing, not cryptographic operations
- Specialized hardware can provide dramatic speedups
- Processing-in-memory architectures eliminate data movement overhead
- Example: Standard CPU performance ~7,700 Falcon signatures/second; specialized hardware can achieve 1,000,000+ signatures/second (140x faster)
Algorithm-specific optimizations:
- Choose algorithms appropriate for domain constraints
- Falcon-512: Smallest signatures (690 bytes) for bandwidth-constrained applications
- ML-DSA: Good all-around performance for general use
- SLH-DSA: When long-term security and algorithmic diversity critical
Domain-specific optimization:
| Domain | Key Constraint | Recommended Approach |
|---|---|---|
| Blockchain | Storage cost | Falcon (smallest signatures) |
| Healthcare (FHIR) | Message throughput | Hardware acceleration |
| Satellite | Bandwidth | Falcon, compression |
| 5G Networks | Authentication speed | Hardware acceleration |
| IoT Sensors | Battery life | Energy-efficient hardware |
| Medical Devices | Battery + Safety | Hardware with fail-safe |
4.5 Test and Validate
Testing methodology:
- Functional testing: Verify correct encryption/decryption, signature generation/verification
- Interoperability testing: Test with different implementations, cross-platform compatibility
- Performance testing: Measure throughput, latency, resource usage under load
- Security testing: Penetration testing, side-channel attack resistance
- Compliance validation: NIST compliance, industry standards
4.6 Monitor and Update
Monitoring strategy:
- Track signature generation/verification rates
- Monitor system latency and throughput
- Measure resource utilization
- Alert on performance degradation
- Log failed verification attempts (potential attacks)
Update strategy:
- Monitor NIST for new standards and recommendations
- Track cryptographic research for vulnerabilities
- Prepare contingency plans if algorithm weakness discovered
- Maintain cryptographic agility for rapid algorithm updates
“Security is not a product, but a process.” ~ Bruce Schneier
5. Real-World Implementation Considerations
5.1 General Implementation Principles
When deploying PQC across different domains, several universal principles apply:
1. Surgical protection: Apply PQC where most critical (high-value operations), not everywhere unnecessarily 2. Hybrid security: Combine classical and PQC during transition for defense-in-depth 3. Minimize disruption: Design solutions that don’t force ecosystem-wide simultaneous upgrades 4. Hardware acceleration: For high-throughput or resource-constrained applications, software-only PQC often insufficient
5.2 Domain-Specific Challenges
Financial Services:
- Challenge: High-frequency trading requires 1M+ signatures/second
- Challenge: Blockchain storage costs make large signatures expensive
- Solution approach: Hardware acceleration for throughput, Falcon for smallest signatures
- Example: Stablecoin platforms implementing dual-signature schemes (classical + PQC) for administrative operations while maintaining user backward compatibility
Healthcare:
- Challenge: HL7 FHIR APIs require high message throughput with compliance auditing
- Challenge: DICOM medical images need integrity verification without workflow impact
- Solution approach: Hardware-accelerated batch verification, message-level signatures
- Example: Hospital systems using 1M+ signatures/second verification to process FHIR bundles in real-time
Telecommunications:
- Challenge: 5G networks require 100K+ device authentications/second
- Challenge: Satellite links have limited bandwidth and high latency
- Solution approach: Hardware acceleration for scale, compact signatures for bandwidth efficiency
- Example: Network equipment using specialized processors to handle authentication at scale
IoT & Infrastructure:
- Challenge: Battery-powered devices need 10-20 year lifespans
- Challenge: Limited memory and processing power
- Solution approach: Energy-efficient hardware (<1 microjoule per operation), firmware updates
- Example: Smart meters and medical implants using secure element chips with native PQC support
5.3 Hardware Acceleration Approaches
Processing-in-Memory (PIM):
- Traditional computing moves data between memory and CPU (70-80% of time)
- PIM computes directly where data resides, eliminating movement overhead
- Particularly effective for lattice-based algorithms (Kyber, Dilithium, Falcon)
- Can achieve 100x+ performance improvements
Secure Element Integration:
- Tamper-resistant chips with embedded PQC acceleration
- Ideal for payment terminals, IoT devices, mobile devices
- Provides hardware root of trust with quantum-safe operations
- Enables cryptographic agility through firmware updates
Implementation example: One approach, developed by companies like BTQ Technologies, integrates PQC acceleration directly into secure element chips, achieving specifications like 5× faster AES, 1M digital signatures/second, and <1 microjoule per operation. Such hardware enables PQC deployment in previously impossible scenarios like battery-powered medical implants and satellite communications.
5.4 Deployment Timeline Best Practices
Typical enterprise timeline:
| Phase | Duration | Activities |
|---|---|---|
| Assessment | 3-6 months | Cryptographic inventory, risk assessment, algorithm selection |
| Pilot | 6-12 months | Non-critical systems, testing, performance validation |
| Production Rollout | 12-24 months | Phased deployment, hybrid mode, monitoring |
| Complete Migration | 24-36 months | Deprecate classical-only, full PQC deployment |
Key milestones:
- By January 2027: New systems must support PQC (CNSA 2.0 requirement)
- By December 2030: Complete phase-out of non-PQC
- By 2035: All systems quantum-resistant (NSM-10 deadline)
5.5 Lessons from Early Implementations
What works:
- Hybrid approaches reduce risk during transition
- Targeting high-value operations first provides quick wins
- Hardware acceleration proves essential for real-time systems
- Backward compatibility crucial for gradual ecosystem adoption
- Standards alignment (NIST) accelerates regulatory acceptance
Common pitfalls:
- Underestimating performance requirements
- Assuming software-only PQC sufficient for all applications
- Neglecting long-term maintenance and algorithm updates
- Forcing simultaneous ecosystem-wide upgrades (usually fails)
- Insufficient testing before production deployment
Success factors:
- Executive sponsorship: Secure budget and resources for multi-year project
- Cross-functional teams: Involve security, development, operations, compliance
- Incremental approach: Start small, learn, scale gradually
- Performance validation: Test thoroughly before production
- Contingency planning: Prepare for algorithm updates or emergency rollbacks
“In the middle of difficulty lies opportunity.” ~ Albert Einstein
6. Safety and Security Considerations
6.1 The Harvest Now, Decrypt Later Threat
HNDL deserves deeper examination as the most immediate quantum security threat.
The attack lifecycle:
Phase 1: Collection (Happening now)
- Adversaries intercept and record encrypted communications
- Blockchain transactions permanently stored (all public)
- VPN traffic, secure messaging, financial transactions captured
- Cost: Minimal (storage is cheap, interception is passive)
Phase 2: Storage (Ongoing)
- Maintain archives of encrypted data
- Wait for quantum computers to become available
- Time horizon: 5-15 years based on Q-Day estimates
Phase 3: Decryption (Future)
- Use quantum computer to break stored encryption
- Derive private keys from public keys
- Decrypt everything collected in Phase 1
Why traditional risk models fail: By the time quantum computers exist, it’s too late—the data was already collected.
Particularly vulnerable data:
- Biometric data (can’t be changed)
- Medical records (sensitive for lifetime)
- Financial records (long-term impact)
- Government secrets (decades-long classification)
- Authentication credentials (reveal patterns)
6.2 Mitigation Strategies
1. Cryptographic Agility
Design systems to rapidly switch algorithms if vulnerabilities emerge:
- Abstract cryptographic operations behind interfaces
- Support multiple algorithms simultaneously
- Use configuration for algorithm selection
- Version all cryptographic protocols
- Plan for emergency algorithm replacement
2. Defense in Depth
Layer multiple security controls:
- Network security (firewalls, intrusion detection)
- Access controls (authentication, authorization)
- Encryption (both classical and PQC)
- Monitoring (anomaly detection, audit logging)
- Physical security (hardware security modules)
3. Key Management Best Practices
Generation:
- Use cryptographically secure random number generators
- Generate keys in secure environments (HSMs when possible)
- Use appropriate key sizes
Storage:
- Never store private keys in plaintext
- Use hardware security modules for high-value keys
- Encrypt keys at rest
- Implement strict access controls
Rotation:
- Establish regular rotation schedules
- Rotate immediately if compromise suspected
- Test rotation procedures regularly
Destruction:
- Securely wipe keys when no longer needed
- Multiple-pass overwrite for magnetic media
- Physical destruction for sensitive systems
4. Implementation Security
Common pitfalls to avoid:
Timing attacks:
- Variable-time operations leak information
- Solution: Use constant-time implementations
Side-channel attacks:
- Power analysis, electromagnetic emanation can reveal secrets
- Solution: Use hardened implementations, shield sensitive operations
Poor random number generation:
- Weak randomness leads to predictable keys
- Solution: Use hardware RNGs, properly seeded CSPRNGs
5. Monitoring and Incident Response
Monitoring:
- Log all cryptographic operations
- Track failed verification attempts
- Monitor for anomalous patterns
- Alert on security events in real-time
Incident response plan:
- Detection: Identify potential security incident
- Containment: Isolate affected systems
- Analysis: Determine scope and impact
- Remediation: Fix vulnerability, rotate keys
- Recovery: Restore normal operations
- Lessons learned: Update procedures
6. Regular Security Audits
Audit scope:
- Code review by qualified cryptographers
- Penetration testing by security professionals
- Compliance validation (NIST, industry standards)
- Configuration review
- Incident response plan testing
Audit frequency:
- Annual comprehensive audits minimum
- Quarterly for high-risk systems
- After significant changes
- Following any security incident
7. User Education and Training
Training topics:
- Threat landscape (quantum computing, HNDL attacks)
- Proper key handling procedures
- Recognizing social engineering attacks
- Incident reporting procedures
- Security best practices
“Security is always excessive until it’s not enough.” ~ Robbie Sinclair
7. Review of Key Concepts
7.1 Cryptography Fundamentals
| Cryptography | The practice of securing information through mathematical transformation. |
| Public-Key Cryptography | Cryptographic system using mathematically related public and private keys. |
| RSA | Public-key algorithm based on difficulty of factoring large numbers. |
| ECDSA | Elliptic curve-based digital signature algorithm. |
7.2 The Quantum Threat
| Quantum Computer | Computer using quantum phenomena to perform certain calculations exponentially faster. |
| Qubit | Quantum bit that can exist in superposition of 0 and 1 simultaneously. |
| Shor’s Algorithm | Quantum algorithm that can efficiently break RSA and ECDSA. |
| Q-Day | The moment when a quantum computer can break current cryptographic systems. |
| HNDL | Attack strategy of collecting encrypted data today to decrypt when quantum computers available. |
7.3 Post-Quantum Cryptography
| PQC | Cryptographic algorithms secure against both classical and quantum computers. |
| Lattice-Based | PQC approach based on finding vectors in high-dimensional lattices. |
| Hash-Based | PQC approach using one-way cryptographic hash functions. |
| ML-KEM (Kyber) | NIST standard for post-quantum key encapsulation. |
| ML-DSA (Dilithium) | NIST standard for post-quantum digital signatures. |
| FN-DSA (Falcon) | Additional NIST digital signature standard (smallest signatures). |
7.4 Implementation
| Cryptographic Inventory | Comprehensive catalog of all cryptographic usage in organization. |
| Algorithm Selection | Process of choosing PQC algorithms based on requirements. |
| Hybrid Cryptography | Using both classical and PQC algorithms simultaneously. |
| Hardware Acceleration | Specialized hardware dramatically speeding up cryptographic operations. |
| Testing | Comprehensive evaluation of PQC implementation. |
7.5 Security
| Cryptographic Agility | System design enabling rapid algorithm replacement. |
| Defense in Depth | Security strategy using multiple layers of controls. |
| Key Management | Practices for secure generation, storage, rotation, and destruction of keys. |
| Side-Channel Attacks | Attacks exploiting physical implementation characteristics. |
“The best time to plant a tree was 20 years ago. The second best time is now.” ~ Chinese Proverb
8. Conclusion
This comprehensive tutorial has explored post-quantum cryptography from foundational principles through practical implementation strategies. We examined how quantum computers threaten current cryptographic systems through Shor’s algorithm and the immediate danger of Harvest Now Decrypt Later attacks. We covered the mathematical foundations of PQC and the NIST-standardized algorithms (ML-KEM, ML-DSA, FN-DSA) that provide quantum resistance.
Key Takeaways
1. The threat is real and immediate:
- Q-Day estimated 2030-2035
- HNDL attacks happening now
- Federal Reserve confirms ongoing threat
2. PQC is practical and deployable today:
- NIST standards published (FIPS 203/204/205)
- Runs on classical computers
- Can be integrated into existing systems
3. Implementation requires careful planning:
- Start with cryptographic inventory
- Prioritize high-value/long-lifecycle systems
- Use hybrid approach during transition
- Plan for 2-5 year migration
4. Performance optimization critical:
- Software-only PQC may not meet requirements
- Hardware acceleration provides 10-100x improvements
- Domain-specific optimization essential
5. Federal mandates create hard deadlines:
- New systems must support PQC by January 2027
- Complete phase-out by December 2030
- All systems quantum-resistant by 2035
Implementation Roadmap
Year 1 (2026):
- Complete cryptographic inventory
- Establish PQC working group
- Select algorithms based on NIST standards
- Pilot deployments on non-critical systems
Year 2 (2027):
- Deploy hybrid cryptography for high-value systems
- Train development and operations teams
- Establish performance baselines
- Achieve CNSA 2.0 compliance
Year 3-5 (2028-2030):
- Scale PQC deployment to majority of systems
- Phase out classical-only cryptography
- Continuous monitoring and updates
- Full regulatory compliance
Year 5-10 (2030-2035):
- Complete PQC migration (NSM-10 deadline)
- Deprecate legacy classical cryptography
- Maintain cryptographic agility
- Document lessons learned
Critical Success Factors
- Act now: Every month of delay exposes data to HNDL attacks
- Consider hardware acceleration: Essential for real-time systems and resource-constrained devices
- Embrace hybrid approaches: Provides safety net during multi-year transition
- Optimize for domain constraints: Financial services, healthcare, telecom, IoT each have unique requirements
- Plan for long lifecycles: Systems deployed today must remain secure until 2040+
- Maintain cryptographic agility: Standards may evolve, vulnerabilities may be discovered
The Path Forward
The quantum threat represents the most significant security challenge in the digital age. But the solution is clear: post-quantum cryptography provides mathematically sound defense, NIST standards are published, practical implementations exist, and regulatory mandates are driving adoption.
Organizations that deploy PQC today will emerge from the quantum transition with security intact and competitive advantage secured. Those that delay risk catastrophic compromise when quantum computers achieve cryptographic relevance.
The transition to post-quantum cryptography requires careful planning, cross-functional coordination, domain-specific optimization, and multi-year execution. The tools exist, the standards are published, and the regulatory mandates are clear.
The time to act is now. The organizations that move decisively today will secure their future in the quantum era.
Disclaimer: References to specific companies or technologies (including BTQ Technologies’ QSSN, CASH, and QCIM solutions) are provided as illustrative examples of implementation concepts and do not constitute endorsements or recommendations. Organizations should evaluate multiple approaches when designing their own PQC solutions.